
Generic metamodels for expressing configurations of (a) DAC; (b) BLP... | Download Scientific Diagram

Generic metamodels for expressing configurations of (a) DAC; (b) BLP... | Download Scientific Diagram
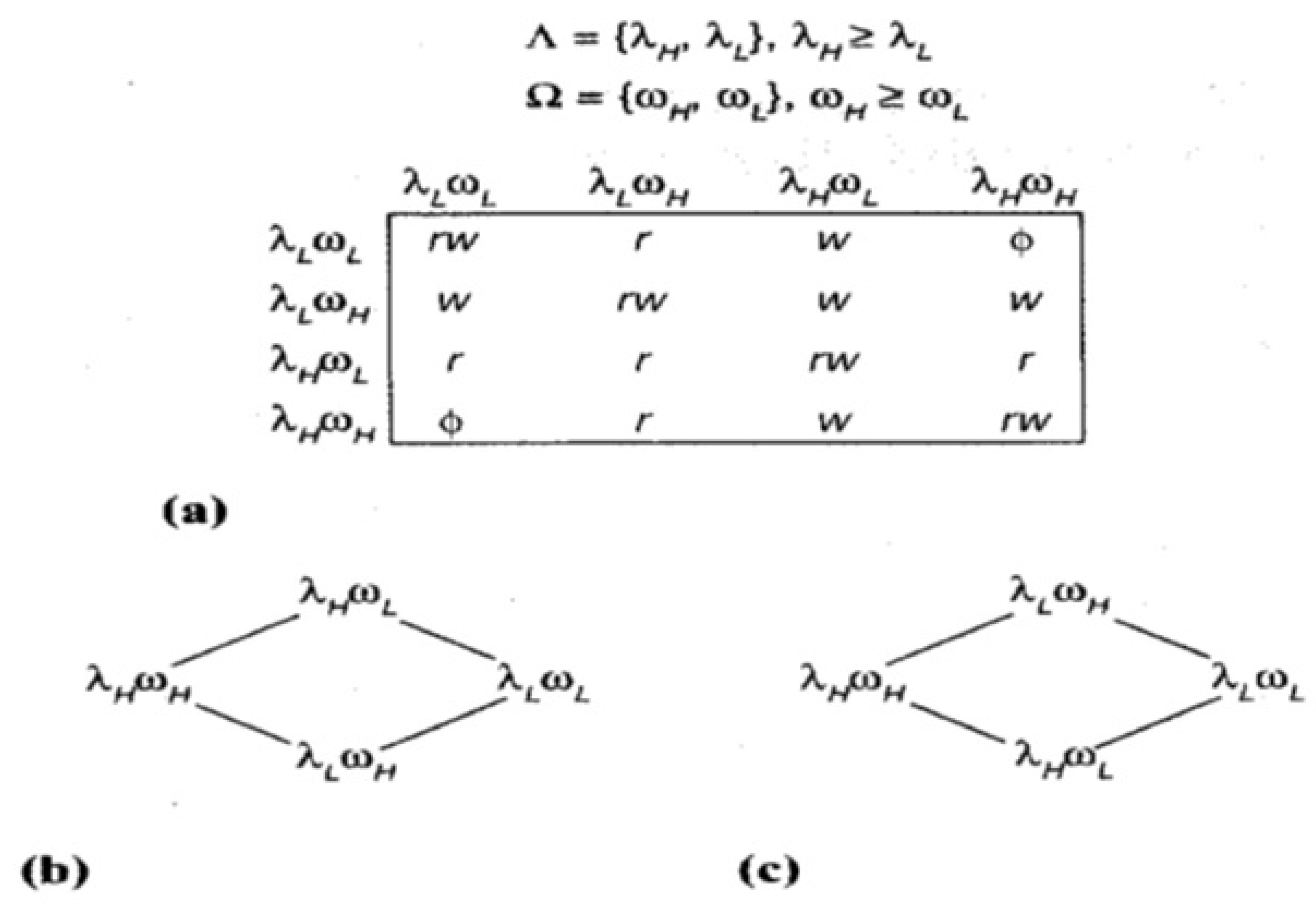
Electronics | Free Full-Text | From Conventional to State-of-the-Art IoT Access Control Models | HTML

Generic metamodels for expressing configurations of (a) DAC; (b) BLP... | Download Scientific Diagram

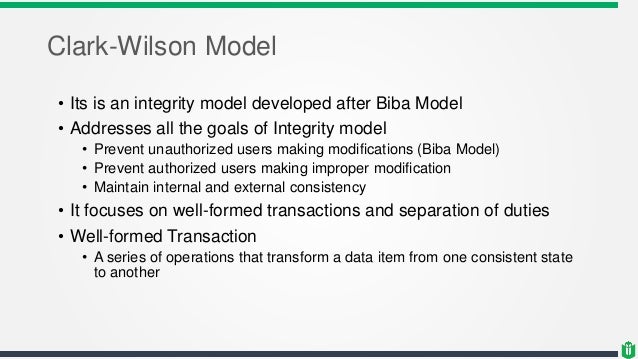
1 Lecture 3 Security Model. 2 Why Security Models? u A security model is a formal description of a security policy u Models are used in high assurance. - ppt download
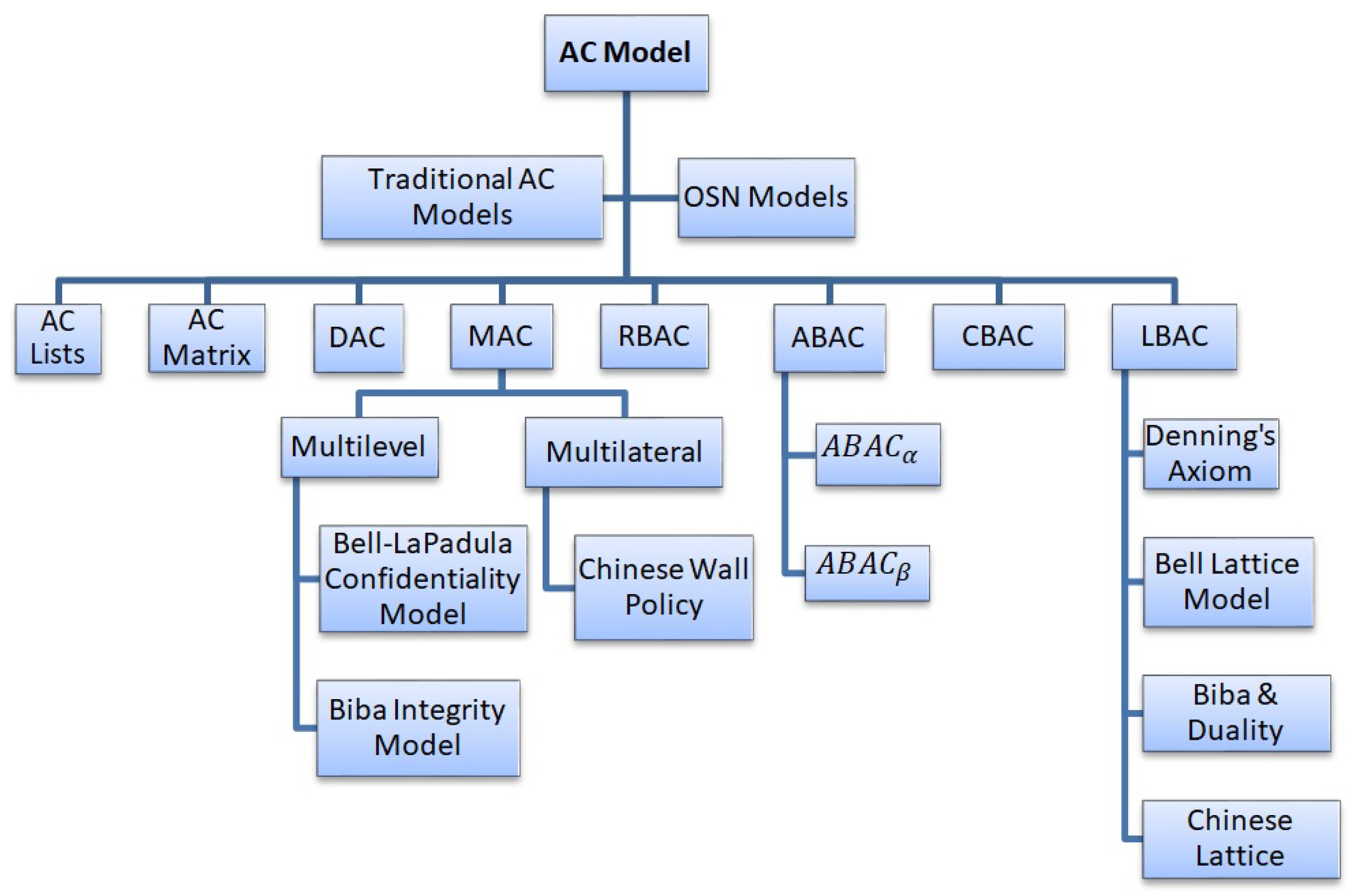
Electronics | Free Full-Text | From Conventional to State-of-the-Art IoT Access Control Models | HTML









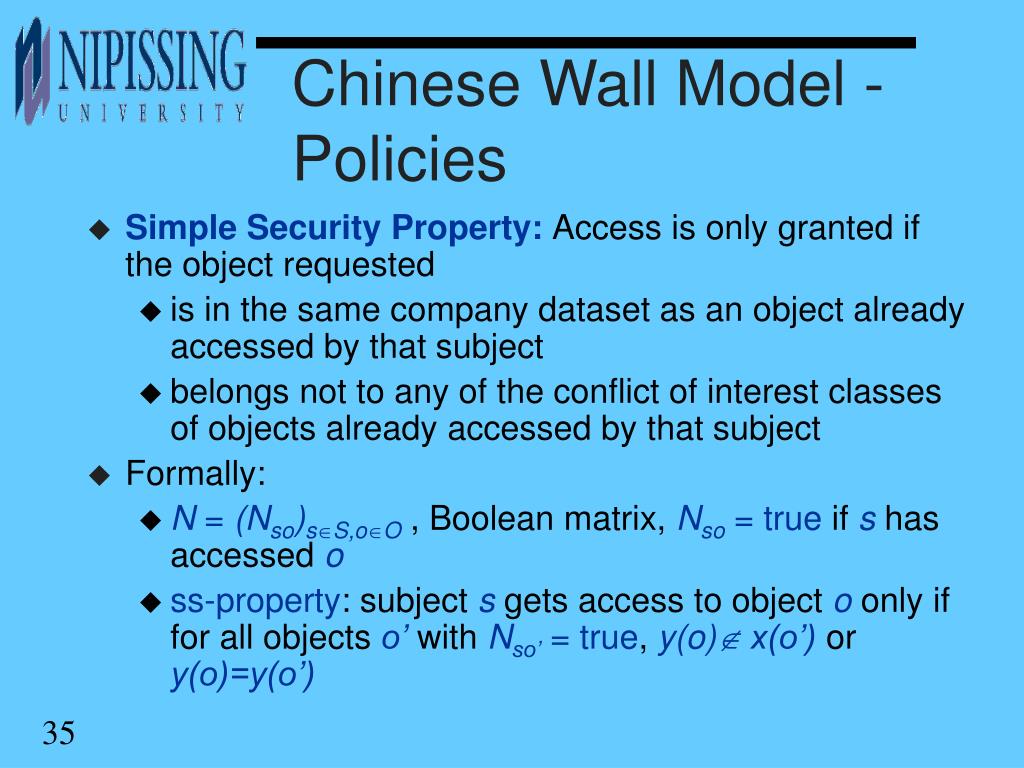

![PDF] Lattice-based access control models | Semantic Scholar PDF] Lattice-based access control models | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/9a0174d303de6edb48be5fefdc3ddffa0d09b029/8-Figure4-1.png)